The Null Device
Posts matching tags 'hacks'
2013/11/1
What happens when computers get cheap enough to be effectively disposable? Well, criminals start embedding penetration servers into dumb electrical goods like irons and kettles. The low-powered machines (which could consist of an exotic embedded OS running on something tiny, though these days, it could just as easily be a Linux distribution running on an ARM or MIPS system-on-a-chip, kitted out with standard Linux hax0r tools) then attempt to connect to any machines within range by WiFi or Bluetooth, find security holes and take them over. Which is the sort of thing you'd expect first-tier intelligence agencies to attempt to try on high-value targets, but it now seems to be in the hands of ordinary criminals.
2013/10/18
Toy of the day: PuzzleScript is an online (browser-based) game development environment capable of making a wide variety of turn-based puzzle games, ranging from Sokoban (of which the Hello World-esque example one starts with is a variant) to more sophisticated and/or eccentric games.
Games are written in a functional/declarative notation, consisting of rules; for example, the Sokoban rule allowing the player to push a crate is written as:
[ > Player | Crate ] -> [ > Player | > Crate ]
Graphics are deliberately kept simple, with elements being 5x5 blocks of coloured pixels, giving the game a vaguely Atari 2600-esque aesthetic.
There is a gallery of games made by users, each with an animated GIF representing the game's play. Some examples:
Games were originally turn-based (in that nothing happened except when the player moved), but there is an experimental real-time feature. Somebody has already coded a (semi-functional and not particularly exciting) Pac-Man clone.
2013/10/1
Jeroen of Spritesmods (who previously built a miniature arcade machine out of a Raspberry Pi) has an interesting piece on the possibilities of hacking the controllers in hard drives; most hard drives these days contain embedded ARM-based systems, often with reasonably powerful processors. (One WD hard drive had two ARM Feroceon cores, similar to ones used in network-attached storage appliances.) It is possible to reprogram the firmware in hard drive controllers, which has a number of defensive, offensive and other applications, from silently patching system files to insert exploits to detecting attempts at drive imaging (such as by police, customs officials or spies) and returning corrupted or falsified data. (I wonder whether algorithmically generating a FAT32 filesystem, empty except for one file named GOATSE.JPG, would be feasible within the memory footprint.) Also, given that broken hard drives with perfectly functional controllers are literally free (they're legally electronic waste that costs money to dispose of correctly), they could possibly serve as a source of free microcontrollers for various projects, such as hobby robots or circuit-bent musical instruments (assuming that one figures out how to make them control things other than hard drives).
2013/8/26
Continuing on from the previous post about Australian Senate how-to-vote cards and who really is preference-swapping buddies with whom, I have spent some time playing around with the D3 web-based data visualisation library, and have managed to build an interactive visualisation of the Senate voting sheets (and, more specifically, the various parties' affinities for each other).
As such, I present to you: the Australian Senate Preference Navigator:
It requires a reasonably modern browser (or at least one with SVG support).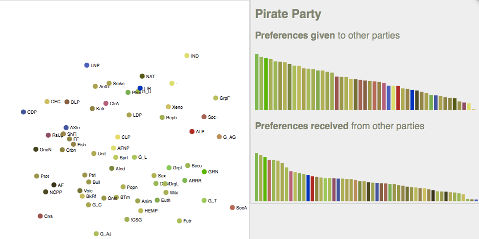
2013/1/31
An interesting article on the genesis of the Roland TR-808, and how Roland's famous line of drum machines owes its existence to an American musician and circuit-bending pioneer named Don Lewis:
Raised with a rich gospel tradition in Dayton, he brought his myriad musical talents to San Francisco in the ‘60s, where he was a staple in nightclubs. His one-man-band became known for its wild array of electronic instrumentation, which was still a novelty in those days — a small truckload of synthesizers and early rhythm boxes accompanied Don’s richly-vocoded tenor to make a sound no one had heard but everyone liked.
Don had been hired by the Hammond organ company to demo its products on the show floor. He was using an Ace Tone rhythm box (which was distributed by Hammond at the time) as his percussion section. "I had modified my Ace Tone to death, changed all the rhythms because none of them fit my style of playing. I also wired it through the expression pedal of the Hammond, so I could get [percussion] accents, which no one was doing then. After the show this man from Japan came up and the first thing out of his mouth was ‘that looks like my rhythm unit but it doesn’t sound like my rhythm unit! How did you do that?’" It was Ikutaro Kakehashi, the president of Ace Tone.Kakehashi went on to found Roland Corporation, capitalising on Lewis' suggestion for a rhythm box with modifiable rhythms (or, what later became known as a drum machine), and hiring Lewis as an engineer, to work on projects including the CR-68 and, eventually, the TR-808.
On a visit to Roland’s Tokyo offices in the late ‘70s, Don was working with chief engineer Tadao Kikumoto. "That day he had a bread board of an 808 and was showing me what was going on inside — he sort of bumped up against the breadboard and spilled some tea in there and all of a sudden he turned it on and got this pssh sound — it took them months to figure out how to reproduce it, but that ended up being the crash cymbal in the 808. There was nothing else like it. Nobody could touch it."The article also describes Lewis' homemade Live Electronic Orchestra, the complex of ancient synthesizers and other circuits which Lewis played live back in the 1960s, and which has been restored for a special performance at the NAMM music trade fair:
It’s a one-off work of art, a kind of who’s who of vintage synthesizers networked to one another through connection standards the industry has long forgotten but Don is still fluent in. A series of hand-built buffer boards and timing modules allow an Arp Pro Soloist to talk to a Promars Computronic and a Roland Jupiter-4. The Hammond expression pedal can control a variety of parameters for any of the sounds coming through the Boss KM-6A mixer, whose channels Don built a remote control panel for right into the body of the three-stage organ. It’s basically a 1977 copy of Ableton Live that weighs two tons, doesn’t have a EULA, and does a heart-melting rendition of "Amazing Grace."
2013/1/21
A software developer in the US has taken outsourcing into his own hands, by hiring a company in China to do his job for less than ¹⁄₅ of his salary:
"This organisation had been slowly moving toward a more telecommuting oriented workforce, and they had therefore started to allow their developers to work from home on certain days. In order to accomplish this, they'd set up a fairly standard VPN concentrator approximately two years prior to our receiving their call," he was quoted as saying on an internet security website.
"Authentication was no problem. He physically FedExed his RSA [security] token to China so that the third-party contractor could log-in under his credentials during the workday. It would appear that he was working an average nine-to-five work day," he added.The unnamed developer is said to have come physically into work but spent the time surfing eBay, Facebook and Reddit and watching cat videos on YouTube for the standard eight hours a day, which somewhat defeats the purpose of his hack. Then again, the report also suggests that he was simultaneously employed at several other companies, and similarly subcontracting his duties there to Shenyang.
The Daily Torygraph's Dr. Tim Stanley has hailed the developer as an exemplar of capitalism at its best:
For not only is Bob a modern hero to the terminally bored office worker, he’s also invented a whole new way of making capitalism work. If big companies can outsource labour to save money, why the heck can’t the little man do exactly the same?His employer, Verizon, didn't agree, and sacked him.
A recent popular self-help book, The Four Hour Work Week by Tim Ferriss, advocated doing the same sort of thing, converting oneself into middleware binding together disparate subcontractors and charging a premium for doing so, though advised the reader to first arrange to be able to work from home. And there are reports of enterprising hackers having done similar things as early as 2004.
On a similar tangent, Britain's sense of moral indignation has also been outsourced to China, and is being handled by “a permanently outraged man working 96-hour shifts” just outside of Beijing:
The outrage outsourcing was first noticed when a Rod Liddle was accidentally printed in its original Mandarin.
2012/12/11
The latest in extreme burrito delivery systems: the Burrito Bomber, an Arduino-powered drone which will drop a burrito on a parachute to your GPS coordinates:
It works like this:A bit like the Alameda-Weehawken Burrito Tunnel, only the authors have actually built it. The only reason for it not being operational (other than questions of whether it'd be economical compared to traditional burrito delivery methods) is because it's not yet legal to commercially operate drone aircraft in the United States.
- You connect to the Burrito Bomber web-app and order a burrito. Your smartphone sends your current location to our server, which generates a waypoint file compatible with the drone's autopilot.
- We upload the waypoint file to the drone and load your burrito in to our custom made Burrito Delivery Tube.
- The drone flies to your location and releases the Burrito Delivery Tube. The burrito parachutes down to you, the drone flies itself home, and you enjoy your carne asada.
2012/3/14
Some hackers in Germany have automated the process of generating semi-random T-shirt designs.
 The result is Zufallsshirt (“chance shirt”), a sort of Borgesian infinite library of quasi-ironic T-shirts. It generates a huge number of combinations of phrases (mostly in German, though with quite a few in English), words and clip-art. Some look like the sort of thrift-store attire hipsters wore 15 years ago, others like miscellaneous ravey wordmarks pumped out by T-shirt labels, and others are rectangles of acrostics of random words.
The result is Zufallsshirt (“chance shirt”), a sort of Borgesian infinite library of quasi-ironic T-shirts. It generates a huge number of combinations of phrases (mostly in German, though with quite a few in English), words and clip-art. Some look like the sort of thrift-store attire hipsters wore 15 years ago, others like miscellaneous ravey wordmarks pumped out by T-shirt labels, and others are rectangles of acrostics of random words.
Some of the results are more presentable than others; one might believe that “Budapest Bicycle Flux” was a semi-obscure math-rock band whose gig the wearer happened to catch in some college-town bar back in the day, and there are situations where one might plausibly wear a T-shirt reading “I Reject Your Reality And Replace It With Cupcakes”, which, alas, cannot be said for some of the outputs, such as “your vagina is a wonderland”, or a grid of words including “Hitlerponys”, “Mörderpenis” and/or the decidedly euphemistic-sounding “wurstvuvuzela”. There are no permalinks and no way of keeping a design other than by buying it (i.e., getting it printed and shipped, which is done by a Leipzig-based mail-order T-shirt printing company). Or by saving the .png file of the image from the website. Anyway, I suspect that the creators have made a fair amount of money, and quite a few people have drawers full of odd-looking shirts from a parallel universe.
Interestingly enough, after clicking through the site for a while, a reader with a limited grasp of German may find their German comprehension improving slightly; perhaps the flood of meaningful (if nonsequiturial) sentences exercises the language pattern-matching parts of the brain in some kind of process of combinatorial fuzzing, reinforcing plausible word sequences.
2011/5/31
A group of hackers in Germany have built a device disguised as a wall-mounted power supply which connects to wireless networks, intercepts packets and subtly changes the content of pages from news websites:
The Newstweek uses ARP spoofing to change the text displayed on several news sites. After doing some field research, placing and configuring the device, there’s a simple web frontend that configures the man-in-the-middle hack. Right now, the Newstweek only allows a few news sites to be targeted, but the team is working on allowing anyone to add their own targets.There is a technical walkthrough of its construction here. Unsurprisingly, it's basically a Linux-based wireless access point, hacked into a new case and running a customised version of the OpenWRT firmware.
Meanwhile, Charlie Stross extrapolates on more serious applications of such technologies:
This sort of gadget is, in bulk, extremely cheap — I bet you could order them for well under $100 in batches of a thousand and up. Say you're a repressive regime, but not so repressive that you can just haul random dissidents off to the torture chamber without paying lip service to due process. How hard would it be to plant these things in your targets' homes, so that you can gaslight them by interfering with the news they're reading? Call it a digital agent provocateur. Say you're the DHS and you want a steady stream of clueless Al Qaida wannabes to arrest and show on CNN to keep everyone afraid enough to go along with your PATRIOT Act extension? Plant these in the homes of young muslim males who hang out at the wrong mosques, crank up the volume of hateful news, and see who snaps ...
2010/12/11
Want to use a Steadicam on your next film but can't afford a real one? Try using a live chicken instead.
2010/7/24
The Chipophone is an instrument for live chiptune performance (i.e., playing live music on a keyboard in the style of music generated by 8-bit computers and game consoles), made from microcontrollers and housed in the chassis of a 1970s-vintage electronic organ by a Swedish chap named Linus Akesson. There is a video of Akesson demonstrating the unit and its features, and playing some classic chiptunes live, here.
2010/7/3
13-year-old Hibiki Kono built a machine allowing him to climb walls; the rig consists of a backpack with two small vacuum cleaners strapped to it, suction pads attached to the nozzles; the pull seems to be strong enough to allow him to climb as high as the power cord lets him. (Meanwhile, some commenters here claim that Kono merely copied somebody else's design without improving or modifying it.)
2010/3/28
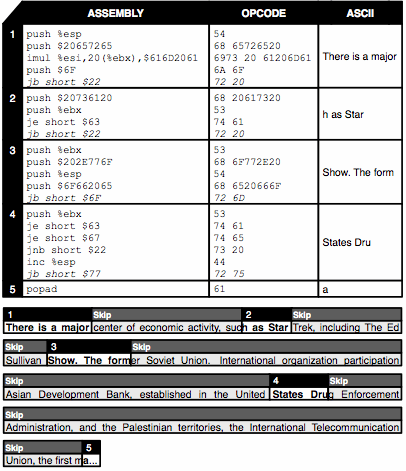
Security researchers are now working on ways of generating machine code that looks like English-language text (PDF).
In this paper we revisit the assumption that shellcode need be fundamentally different in structure than non-executable data. Specifically, we elucidate how one can use natural language generation techniques to produce shellcode that is superficially similar to English prose. We argue that this new development poses significant challenges for inline payloadbased inspection (and emulation) as a defensive measure, and also highlights the need for designing more efficient techniques for preventing shellcode injection attacks altogether.The code is generated by a language engine which selects fragments of text, Markov-chain-fashion, from a large source (such as Wikipedia or the Gutenberg Project). It looks like the random gibberish spammers pad their emails out with, though if executed, functions as x86 machine code. (Rather inefficient machine code, with a lot of jumps and circumlocutions to fit the constraints of looking like English, but good enough to sneak exploits through in.) Below is an example of some code thus disguised:
2010/3/14
Seen at Maker Faire: Two guys from ARM (the people who designed the CPU in your mobile phone and probably a dozen other devices you own) have designed an amazingly elegant new microcontroller prototyping board, for making electronic gadgets even more easily than with the Arduino. Called mbed, it consists of a board with a USB port and 40 pins. The pins do the usual things (analogue/digital I/O, USB, Ethernet, &c.), but that's not the impressive thing about it; the impressive part is the design of the whole system, which brings web-style agile development to microcontroller-based gadgets.
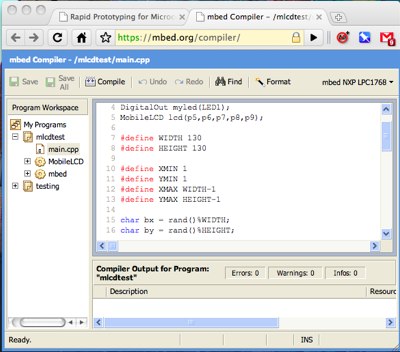 When you get an mbed, you plug it into your computer (which may be a Windows PC, a Mac, a Linux box or anything else which can mount USB drives); it then appears as a USB disk, containing one file: a web link. You go to the web link, which directs you to mbed's web site, where you log in or create an account; from then on, you have an integrated development environment in your browser, with source navigation, syntax highlighting and a compiler. Your code is hosted online on mbed's servers (the system uses the Subversion version control system as a store). Create a new project, and you get a "Hello World" program (written in C++) which, by default, flashes one of the mbed board's built-in LEDs. Hit the Compile button, and your browser soon prompts you to download a .bin file of the compiled program. Save it to the mbed card's drive, hit the reset button on it, and your program runs.
When you get an mbed, you plug it into your computer (which may be a Windows PC, a Mac, a Linux box or anything else which can mount USB drives); it then appears as a USB disk, containing one file: a web link. You go to the web link, which directs you to mbed's web site, where you log in or create an account; from then on, you have an integrated development environment in your browser, with source navigation, syntax highlighting and a compiler. Your code is hosted online on mbed's servers (the system uses the Subversion version control system as a store). Create a new project, and you get a "Hello World" program (written in C++) which, by default, flashes one of the mbed board's built-in LEDs. Hit the Compile button, and your browser soon prompts you to download a .bin file of the compiled program. Save it to the mbed card's drive, hit the reset button on it, and your program runs.
That's not all, though; the mbed card can work with a plethora of hardware modules, from Nokia-style LCD displays to GPS units, Bluetooth modems and more. Which is where the next bit of elegance comes in. There exists an ecosystem of modular classes for driving these various devices. To attach a supported device, all you have to do is add the class for it to your project (by pasting the URL of its Subversion repository into a dialog box; the IDE does the rest for you), instantiate it as an object and call its methods. For example, here is code for drawing on a Nokia-style LCD display:
MobileLCD lcd(p5,p6,p7,p8,p9); // the I/O pins
lcd.background(0xffff99);
lcd.foreground(0x000000);
lcd.locate(2,2);
lcd.printf("Hello world\n");
lcd.fill(0,64,128,128, 0xffffff);
mbed is somewhat more expensive than the Arduino (the price quoted was about £45 for the mbed board itself, whereas Arduino-compatible boards go for £13 or so). However, the elegance of the design, its ease of use and sheer niftiness could make it worth the price.
2010/2/27
When the Chumby One internet widget terminal was being assembled, the company noticed that one batch of memory cards, from Kingston, had a lot of defective cards. (The Chumby One's internal storage is a MicroSD card, like the ones used in mobile phones.) Kingston refused to replace them, as they had been programmed, and it looked like Chumby were out of luck. However, Chumby had an ace up their sleeve: one of their vice presidents is Andrew "Bunnie" Huang, i.e., the guy who cracked the XBox, and not someone one should count on being able to pull one over.
Anyway, Bunnie noticed some irregularities in the cards' markings and decided to conduct a thorough forensic investigation, examining the cards' serial numbers and manufacturing dates (where he found more inconsistencies; a lot of cards with implausibly low serial numbers and mismatched manufacturers' IDs) and then dissolving the cards' casings to examine their construction, and unearthed some answers:
First, the date code on the irregular card is uninitialized. Dates are counted as the offset from 00/2000 in the CID field, so a value of 00/2000 means they didn’t bother to assign a date (for what it’s worth, in the year 2000, 2GB microSD cards also didn’t exist). Also, the serial number is very low — 0×960 is decimal 2,400. Other cards in the irregular batch also had similarly very low serial numbers, in the hundreds to thousands range. The chance of me “just happening” to get the very first microSD cards out of a factory is pretty remote. The serial number of the normal card, for example, is 0×9C62CAE6, or decimal 2,623,720,166 — a much more feasible serial number for a popular product like a microSD card. Very low serial numbers, like very low MAC ID addresses, are a hallmark of the “ghost shift”, i.e. the shift that happens very late at night when a rouge worker enters the factory and runs the production machine off the books. Significantly, ghost shifts are often run using marginal material that would normally be disposed of but were intercepted on the way to the grinder. As a result, the markings and characteristics of the material often look absolutely authentic, because the ghost material is a product of the same line as genuine material.After confronting Kingston and getting an exchange, no questions asked, Bunnie didn't stop investigating, visiting the dodgy bazaars of China and dealing with characters straight out of cyberpunk novels to procure a selection of variously dubious cards to investigate, and discovering various truths, some less savoury than others, about the memory card market. (For one, memory cards cost about as much as the raw memory inside them, but also contain an ARM-based microcontroller which is thrown in for free; the microcontroller handles error testing and saves the manufacturer the cost of dedicated testing gear, whilst also allowing the users of the card to get away with using regular filesystems on them. Secondly, some manufacturers, pressed to cut costs and increase profit margins, appear to be sanctioning (or at least turning a blind eye to) ghost shifts with dodgy materials and pawning the brummagem batches off on the kinds of weaker players they don't have much to fear from.)
Ghost shifts, and unlicensed extra items made on the side, are not unique to the memory card industry; this article describes several cases of contract manufacturers churning out extra copies of goods on the side, often in quantities large enough to flood markets, including a case involving shoe company New Balance.
Of course, you probably won't find ghost-shifted iPhones (as opposed to actual fake pseudo-iPhones, with built-in FM radios and entirely different firmware styled to look more or less iPhone-like) on the market any time soon, as Apple play hardball with their contractors, insisting on draconian security measures, dividing the manufacturing process up between different companies, and using nonstandard components.
2010/2/24
An unemployed sysadmin in Russia hacked into a video billboard and reprogrammed it to show a pornographic video, causing a traffic jam as drivers on a nearby road stopped to gape at the video and record it with their mobile phones.
The hacker, from Novorossiisk, used a server in Chechnya in an attempt to cover his tracks, though was unsuccessful; the Interior Ministry managed to track him down. (I wonder whether he'd have had more luck had he chosen a less politically fraught staging point.) He is now facing two years imprisonment; meanwhile, security rules for video billboards have been tightened.
I'm thinking something like this would make a good plot device; imagine a gang of assassins/bank robbers planting logic bombs in a few strategically placed billboards; at a preset time, they start showing porn, causing instant traffic jams and trapping their victim/blocking their pursuers. Or international jewel thieves hack video screens in an exclusive reception to show Goatse-style shock porn; as the attendees are momentarily stunned by the shock, unable to react, the bandits (dressed as waiters, naturally) act quickly, snatching the valuables and making their escape. Police have a hard time piecing together what happened afterward.
(via Boing Boing) ¶ 2
2010/1/20
An Armenian-born programmer recounts how, during his childhood in the USSR, he stumbled across the KGB's technique for listening in on conversations in any home.
Some time in 1981, I think, a relative from the U.S. comes to visit us for the first time since he left the country many years before that. He was going to stay in our house for a couple of weeks. My parents told me that such visits were always "monitored" by KGB, and so I should be careful with expressing any kind of anti-soviet ideas (which I was known for in the school). In the end though, nobody was going to take this seriously: neither the possibility of KGB agents freezing in cold outside watching us through the windows, nor any kind of bugs installed in our house.
Something strange, however, had happened when our relative had finally arrived. Our phone went crazy. First of all, it was practically impossible to call or to take calls during that period. And besides, the phone's ringer started giving a single "ding" twice a day, exactly at 9 in the morning and 9 in the evening.The KGB, it seems, was using the ringers of telephones as crude microphones, responding to sound vibrations and feeding a very weak signal back into the phone line; when a house was noted as being of sufficient interest, a powerful amplifier could make the signal just about intelligible. The KGB only got caught out (to the extent of allowing a young boy to figure out what was happening, at least) due to the dilapidated condition of the Soviet phone system, and the tendency for lines to get crossed from time to time.
2010/1/18
A Russian CCTV surveillance company has allegedly stumbled along an ingenious way of reducing operating costs and boosting profits: by replacing surveillance camera feeds with prerecorded video. The alleged fraud was uncovered during a routine check of cameras in Moscow; the director of the surveillance company, who has been detained by police, denies the claims, claiming it's a setup by rivals.
2009/12/18
US troops in Iraq now have an iPhone app for tracking insurgents; well, for displaying tactical maps in real time. Meanwhile, the insurgents have found a Russian-designed program which can be bought for $26 and which allows them to watch the video feeds of Predator drones, which happen to be unencrypted. (Oops!) The military is planning to fix this, though it's harder to do than it sounds due to the expensive proprietary design of the aging drones.
2009/12/9
Boing Boing has a post on innovative ways of gaming airlines' pricing and air-miles schemes:
I love hanging out in airmile hacker forums -- these folks are insane. My favorite is the British Airways "Lisbon Loop." BA wants to court continental passengers, so trips overseas that originate from continental Europe are much cheaper. BA flight hackers claim that they buy a BA ticket that goes Lisbon-London-NYC-London-Lisbon, and a one-way cheap EasyJet ticket to Lisbon so they can board it. On the way home, they just get off in London, saving a bundle (you can't skip the Lisbon-London leg, or BA will cancel your tickets).The ostensible topic of the post is, alas, somewhat more prosaic: a way of getting free air miles by buying US dollar coins and using them to pay off the credit card bills (through a loophole which has now apparently been closed).
2009/10/9
An electronic composer in Vienna has developed a means of reproducing the human voice on a piano. Recordings of speech are analysed and converted to frequency data, which is turned into MIDI notes. When played on a grand piano (using a system consisting of 88 pencil tops pushed by electromagnets or motors), it sounds intelligible, though otherworldly.
2009/4/22
Users of criminal hacking forums have apparently been offering ridiculous sums of money for one type of low-end mobile phone. Certain Nokia 1100 handsets, manufactured in Bochum, Germany, are said to have a firmware bug which allows them to be reprogrammed to use another user's phone number, and thus intercept text messages containing bank transaction authentication codes, which is why the going price for them has gone as high as €25,000. Nokia have denied knowing of either such a flaw or of the phones for going for more than €100.
Though if criminals want a handset that can bypass GSM network security and intercept other users' messages, surely there'd be cheaper ways to go about this. Given that criminal gangs somehow managed to compromise a Chinese factory that made point-of-sale terminals and "enhance" the terminals with GSM-based card skimmers, surely it wouldn't be so hard to get one of the numerous Chinese mobile phone manufacturers to intentionally weaken security in one of their units to allow it to be used to spoof numbers, and then buying up a few boxloads of them. Bonus points for getting one that looks almost like an iPhone.
2009/4/20
In Brazil, the street finds its own uses for obsolescent US military satellites. For over a decade, Brazilians, from long-haul truck drivers and villagers out of the reach of the mobile phone networks of the cities to illegal loggers and organised crime factions, have been bouncing radio signals off a US Navy satellite system using jury-rigged off-the-shelf amateur radio equipment. The satellite system, known as FLTSATCOM to its owners, is colloquially referred to as "Bolinha", or "little ball".
To use the satellite, pirates typically take an ordinary ham radio transmitter, which operates in the 144- to 148-MHZ range, and add a frequency doubler cobbled from coils and a varactor diode. That lets the radio stretch into the lower end of FLTSATCOM's 292- to 317-MHz uplink range. All the gear can be bought near any truck stop for less than $500. Ads on specialized websites offer to perform the conversion for less than $100. Taught the ropes, even rough electricians can make Bolinha-ware.
Truck drivers love the birds because they provide better range and sound than ham radios. Rogue loggers in the Amazon use the satellites to transmit coded warnings when authorities threaten to close in. Drug dealers and organized criminal factions use them to coordinate operations.
When real criminals use these frequencies, it's easy to tell they're hiding something, but it's nearly impossible to know what it is. In one intercepted conversation posted to YouTube, a man alerts a friend that he should watch out, because things are getting "crispy" and "strong winds" are on their way. Sometimes loggers refer to the approach of authorities by saying, "Santa Claus is coming," says Brochi.One problem for the users is that the US military is still using the satellites (a replacement network isn't due online until later this year), and don't appreciate their communications being degraded by cheering football fans and random dodgy dealers. Bolinha activity is illegal, both in Brazil, and the US, and the authorities don't have too many problems triangulating the signals.
The crackdown, called "Operation Satellite," was Brazil's first large-scale enforcement against the problem. Police followed coordinates provided by the U.S. Department of Defense and confirmed by Anatel, Brazil's FCC. Among those charged were university professors, electricians, truckers and farmers, the police say. The suspects face up to four years and jail, but are more likely to be fined if convicted.("Operation Satellite?" Either something got lost in translation, or the people who name operations at the Brazilian federal police aren't the most imaginative bunch. Surely high-level operations should have cryptic, vaguely abstract names, redolent either of neo-Classical grandeur or square-jawed military machismo, like, say, "Operation Prometheus" or "Piranha December Blue" or something. But "Operation Satellite?")
In February of last year, FCC investigators used a mobile direction-finding vehicle to trace rogue transmissions to a Brazilian immigrant in New Jersey. When the investigators inspected his radio gear, they found a transceiver programmed to a FLTSAT frequency, connected to an antenna in the back of his house. Joaquim Barbosa was hit with a $20,000 fine.
(via Boing Boing) ¶ 0
2009/1/14
An interesting interview with a former Windows adware author, by all accounts a very smart guy (albeit of, shall we say, above-average ethical flexibility), exposing both the security exploits used by Windows malware, the arms races in the malware underground and the dodgy business models of the industry:
The good distributors would say, ‘This is ad-supported software.” Not-so-good distributors actually did distribute through Windows exploits. Also, some adware distributors would sell access. In their licensing terms, the EULA people agree to, they would say “in addition, we get to install any other software we feel like putting on.” Of course, nobody reads EULAs, so a lot of people agreed to that. If they had, say, 4 million machines, which was a pretty good sized adware network, they would just go up to every other adware distributor and say “Hey! I’ve got 4 million machines. Do you want to pay 20 cents a machine? I’ll put you on all of them.” At the time there was basically no law around this. EULAs were recognized as contracts and all, so that’s pretty much how distribution happened.
So we’ve progressed now from having just a Registry key entry, to having an executable, to having a randomly-named executable, to having an executable which is shuffled around a little bit on each machine, to one that’s encrypted– really more just obfuscated– to an executable that doesn’t even run as an executable. It runs merely as a series of threads. Now, those threads can communicate with one another, they would check to make sure that the BHO was there and up, and that the whatever other software we had was also up.
There was one further step that we were going to take but didn’t end up doing, and that is we were going to get rid of threads entirely, and just use interrupt handlers. It turns out that in Windows, you can get access to the interrupt handler pretty easily. In fact, you can register with the OS a chunk of code to handle a given interrupt. Then all you have to do is arrange for an interrupt to happen, and every time that interrupt happens, you wake up, do your stuff and go away. We never got to actually do that, but it was something we were thinking we’d do.He also talks about making his registry entries unremovable by using obscure Unicode APIs to add them and putting in characters illegal to the ASCII-based APIs most of Windows uses (oops!), writing device drivers to further pwn the hapless users' machines, and also deploying more Scheme runtime than probably anyone else:
There was also of course Scheme. Eventually, we got sick of writing a new C program every time we wanted to go kick somebody off of a machine. Everybody said, “What we need is something configurable.” I said, “Let’s install a Turing-complete language,” and for that I used tinyScheme, which is a BSD licensed, very small, very fast implementation of Scheme that can be compiled down into about a 20K executable if you know what you’re doing.
Eventually, instead of writing individual executables every time a worm came out, I would just write some Scheme code, put that up on the server, and then immediately all sorts of things would go dark. It amounted to a distributed code war on a 4-10 million-node network.So not only is a botnet of pwned Windows PCs likely to be the world's most powerful supercomputer (in purely numerical terms, at least), but a network of dodgy adware could well have been the peak of Scheme's deployment in the real world.
The author's advice to anyone wanting to avoid adware is "um, run UNIX".
2008/12/1
Got an iPhone you want to get unlocked? The software unlocks for the 3G might not be out yet, though you could always go to Vietnam, where they do things the hardcore way:
First, a technician opened up the phone and stripped it to the motherboard. In his skillful hands, the device seemed much easier to dismantle than I expected.
The technician then extracted the baseband chip, the component that controls the connection between the phone and the mobile network, from the motherboard. (This is a painstaking task as the chip is strongly glued to the phone's motherboard. A mistake during this process could brick the phone completely.)
Once the chip was extracted, it was Tuan Anh's turn. He used a chip reader to read information into a file. He then used a Hex editor to remove the locking data from the file, and after that, the chip got reprogrammed with the newly altered file. Now it was no longer programmed to work with only a specific provider.
The chip then got reassembled into the motherboard, another painstaking process.The entire procedure will cost you about US$80 plus however much travel to Vietnam costs. Mind you, you then have to be careful about not updating your phone, because Apple's updates will re-lock the baseband chip, necessitating a return visit.
2008/10/17
Several researchers at UIUC have written a paper on how one could insert general-purpose back doors into a CPU, allowing those in the know to pwn any machine running on it, almost undetectably:
We present the design and implementation of Illinois Malicious Processors (IMPs). There is a substantial design space in malicious circuitry; we show that an attacker, rather than designing one specific attack, can instead design hardware to support attacks. Such flexible hardware allows powerful, general purpose attacks, while remaining surprisingly low in the amount of additional hardware. We show two such hardware designs, and implement them in a real system. Further, we show three powerful attacks using this hardware, including login backdoor that gives an attacker complete and highlevel access to the machine. This login attack requires only 1341 additional gates: gates that can be used for other attacks as well. Malicious processors are more practical, more flexible, and harder to detect than an initial analysis would suggest.And here are some details:
Our memory access mechanism provides hardware support for unprivileged malicious software by allowing access to privileged memory regions. Malicious software triggers the attack by forcing a sequence of bytes on the data bus to enable the memory access circuits. This sequence can be arbitrarily long to avoid false positives, and the particular sequence must be agreed upon before deployment. Once the sequence is observed, the MMU in the data cache ignores CPU privilege levels for memory accesses, thus granting unprivileged software access to all memory, including privileged memory regions like the operating system’s internal memory. In other words, loading a magic value on the data bus will disable protection checking. We implement this technique by modifying the data cache of our processor to include a small state machine that looks for the special sequence of bytes, plus some additional logic in the MMU to ignore privilege levels when malicious software enables the attack.
Using the shadow mode mechanism, we implement a malicious service that acts as a permanent backdoor into a system (Figure 2). To initiate the attack, an attacker sends an unsolicited network packet to the target system and the target OS inspects the packet to verify the UDP checksum. The act of inspecting the packet (necessary to decide if it should be dropped) triggers the trojaned hardware, and the malicious service interprets the contents of the packet as new firmware that it loads into the processor invisibly. The target operating system then drops the unsolicited packet and continues operation, oblivious to the attack.And there's more, including ways of stealing passwords.
And if civilian security researchers have just discovered this, it's not unlikely that ones in intelligence agencies have had such techniques for a while. I wouldn't be surprised if the NSA had similar back doors in all US-designed CPUs likely to end up on the export market, just in case, or if the Chinese government had similarly altered CPUs (or other strategic components) being manufactured on Chinese production lines, or indeed if other intelligence agencies had managed to get their own hooks into the silicon.
2008/7/8
One of the things I enjoy doing is creating electronic music, for which I use a Macintosh laptop, some music software and various plugins. For the past few years, the software which I used has been Apple's Logic Express, to which I switched from Cubase VST when moving from MacOS 9 to OSX. As Logic didn't come with a drum machine program back then, I found myself buying Linplug's RMIV drum machine, which I have over the years used extensively.
RMIV is an excellent and comprehensive drum machine, which contains both analogue-style drum synthesisers and sample playing capabilities, as well as filters and effects. However, it has one downside; when you import sounds into it, it has the annoying tendency of saving those in its own proprietary format (rather than using a standard format such as, say, AIFF or WAV, both of which are good enough for other software including Apple's own samplers).
Recently I have started using Ableton Live, and have found it very impressive. While Live will happily load all my AudioUnit plugins, it also contains its own drum sample player, Drum Rack, which integrates more tightly with it. Drum Rack allows you to drag your favourite samples to various pads and play them. The hitch is that the samples must be in a standard format; if most of your drum samples are in RMIV's .D4T format, then you have a problem. Guess where most of my samples were?
Anyway, not being one to give up easily, I took it upon myself to examine the D4T format, and come up with a way of converting my samples to an open format. Luckily, I had some samples sitting around in both formats; after examining them with hexdump(1) and a Python interpreter, I soon determined that D4T is a fairly simple format, consisting of a short header and the samples in 32-bit float format.
The header turned out to be a bit more work; there were what looked like magic numbers in it, as well as some values roughly proportional to the file size, though bizarrely unrelated to actual sizes. After creating a few oddly-sized AIFF files, importing them into RMIV and examining the imported versions, I determined that RMIV's format used a bizarre way of encoding integers: it would encode them in binary-coded centimal. Which is to say, as a series of bytes, each containing a value from 1 to 99, representing a pair of decimal digits. Why they settled on this peculiar and inefficient encoding, I can only guess; it seems too feeble to be an attempt to thwart reverse engineering.
Anyway, the point of this anecdote is that I have now written a Python script which converts from RMIV's .D4T sample files to AIFF files. (One could change it fairly trivially to make WAV files, though that's left as an exercise to the reader.) The script, named "dermiv", is here.
2008/1/11
14-year-old "electronics genius" in Lódz, Poland, built a remote control for the city's tram system (apparently out of a TV remote control, though presumably they mean that he housed it in a TV remote control case ) and used it to change points, forcing trams onto the wrong tracks, until he was arrested.
"He had converted the television control into a device capable of controlling all the junctions on the line and wrote in the pages of a school exercise book where the best junctions were to move trams around and what signals to change.
Problems with the signalling system on Lodz's tram network became apparent on Tuesday when a driver attempting to steer his vehicle to the right was involuntarily taken to the left. As a result the rear wagon of the train jumped the rails and collided with another passing tram. Transport staff immediately suspected outside interference.
2007/11/22
One useful feature which Facebook, the social network site of the moment, lacks is the ability to compartmentalise information. Whereas on LiveJournal you can define filters and make posts visible to only some of them, on Facebook, every piece of information you published is visible to all your contacts. (Except for those who can only see a limited profile, who are forever stuck in a purgatory of sort-of being "friends" with you whilst being left out of all the fun.)
Being able to compartmentalise your information is useful; there are undoubtedly things you want to tell some of your friends whilst not letting the rest know, other things you're happy sharing with a different (though possibly overlapping) subset, and others you're happy letting anyone know. Think, for example, of talking about work without pissing off coworkers, or confiding about your lovelife, or discussing health issues without overwhelming others with "too much information". As social software becomes an integral part of the social support networks of today's compulsively multitasking, digitally connected population, such controls become more a necessity than a luxury.
Fortunately, Facebook's users have come up with a workaround: creatign members-only groups in lieu of privileged posts. So next time you see a group with an otherwise uncompelling name like "Emma has a new phone number", you'll know what's going on.
2007/9/12
Some enterprising hackers have reverse-engineered the firmware on a range of Canon digital cameras (based on the DiGIC II chip) and written their own firmware enhancement. Named CHDK, it offers features including RAW images (disabled in non-professional models), live histograms, depth-of-field calculations and a scripting language (based on BASIC, though we can't have everything) that can be used for automating your camera. There are some sample scripts here, which do things from setting bracketing to specialised modes for unusual photographic conditions to automating HDR photography.
What's more, the replacement isn't a new firmware per se, but rather a patch which boots from the memory card and runs from the camera's RAM (apparently making use of the original firmware's functions), so you won't brick your camera.
I wonder, though, what the performance tradeoffs of using it is; I don't imagine that compact cameras would have large amounts of RAM to spare that can be loaded up with third-party software that they were never intended to run in production.
2007/7/4
This guy attached a digital camera (a specially modified keychain camera) to his cat's collar and recorded the sequences of images as the cat (named Mr. Lee) went about his daily journeys. The images vary in quality (as one might expect), and include a lot of obscure nooks and crannies of the sorts cats frequent, and quite a few meetings with other neighbourhood cats.
The author of the page, J. Perthold, also sells cat-mountable digital cameras of his design for people who want to photograph what their cats are seeing. The next step, I imagine, would be to integrate wireless networking capabilities of some sort into the unit and set up a catlog.
2007/4/22
Security researchers have found that it is trivially easy to transmit false traffic reports to in-car navigation units. The units look for messages transmitted as digital data piggybacked onto FM radio signals using a protocol known as RDS, and it seems not to have occurred to whoever designed the RDS system that anyone might tamper with these messages; as such, they are transmitted in the clear, and without any sort of authentication. The units also scan the entire FM spectrum, looking for anything that looks like a radio station with a RDS channel containing traffic information. The rest is left as an exercise to the reader:
Through trial and error, they discovered that transmitting certain code numbers translates into certain warnings that are displayed on the satellite navigation system. Some were amusing. One code number alerts users that there's a bull fight in progress. Another one indicates delays due to a parade. But some weren't so funny. One tells users that there has been a terrorist incident. Another indicates a bomb alert and another an air crash.
2007/3/26
A web site on hacking the AppleTV, Apple's new TV set-top box, which appears to be a low-power Intel-based machine running a customised distribution of otherwise standard OSX. Unlike the iPhone, it seems that it doesn't require executable code to be cryptographically signed. So far, there are instructions on enabling SSH for logging into the AppleTV, installing DivX decoders and the VLC media player and copying things like Apache from an Intel Mac to the AppleTV.
2006/11/9
Cognitive neuroscience researcher Ogi Ogas describes how he used techniques from neuroscience to win a quiz show, getting questions he did not consciously know the answer to:
Cognitive models developed by my advisor Gail Carpenter suggest that a more effective way to evaluate an intuition is to consider its mnemonic associations. If you can mentally trace some of the cognitive links of an intuition (through a process similar to priming), these links may suggest whether the intuition is meaningfully connected to the correct answer or whether the link is trivial, incidental, or wrong. For example, given the question "Bucharest is the capital of what European country?", you might have an intuition that the answer is Hungary, because the actual capital of Hungary--Budapest--sounds like "Bucharest" and is thus unconsciously linked. In this case, naively following your unexamined intuition would lead you away from the correct response: Romania.
My $250,000 question presented me with a case of pure intuition. "The department store Sears got its start by selling what specific product in its first catalog?" Since pop culture esoterica and business origins are outside my domains of interest, I did not know the answer. But for some reason, even before the four possible answers appeared, I thought of watches. When "watches" turned up as one of the choices, I reflected on it further. I did not feel any certainty. But why did my brain come up with "watches?" ... As I concentrated on my watch intuition, I began to think about railroads. My brain's memory pattern of watches was somehow linked to a memory pattern of railroads, and my railroad memory also evoked a memory of Sears. Though I still could not work out the explicit connection between watches and Sears, I satisfied myself that "watches" had some deep mnemonic relationship to both railroads and Sears--perhaps at some point in my life I had read that Sears originally delivered their watch catalogs by railroad?
Later, in the tranquility of my apartment, I discovered that 23-year old railroad station agent Richard Sears sold watches to other station agents along the Minneapolis and St. Louis Railway for a full year before meeting up with Alvah C. Roebuck. I never did discover how this obscure factoid had left its faint trace upon my brain.
2006/10/2
Rock, Paper, Scissors may sound to the casual observer like a perfect game of chance; however, with the human mind being what it is, there are many ways to play it to win:
In RPS circles a common mantra is "Rock is for Rookies" because males have a tendency to lead with Rock on their opening throw. It has a lot to do with idea that Rock is perceived as "strong" and forceful", so guys tend to fall back on it. Use this knowledge to take an easy first win by playing Paper. This tactic is best done in pedestrian matches against someone who doesn't play that much and generally won't work in tournament play.
When playing with someone who is not experienced at the RPS, look out for double runs or in other words, the same throw twice. When this happens you can safely eliminate that throw and guarantee yourself at worst a stalemate in the next game. So, when you see a two-Scissor run, you know their next move will be Rock or Paper, so Paper is your best move. Why does this work? People hate being predictable and the perceived hallmark of predictability is to come out with the same throw three times in row.
When playing against someone who asks you to remind them about the rules, take the opportunity to subtly "suggest a throw" as you explain to them by physically showing them the throw you want them to play. ie "Paper beats Rock, Rock beats scissors (show scissors), Scissors (show scissors again) beats paper." Believe it or not, when people are not paying attention their subconscious mind will often accept your "suggestion". A very similar technique is used by magicians to get someone to take a specific card from the deck.
2006/9/8
Today's novel use of technology: using the vibration detectors in PC hard disks around the world to detect earthquakes and predict tsunamis:
As part of their operation, hard disks measure vibrations in order to keep the read-write head of the disk on track. These measurements can be read from some hard disks. The Tsunami Harddisk Detector captures this vibration data and shares it with computers in other locations connected via a peer-to-peer network to determine whether an earth tremor is occurring.
2006/9/5
Apparently it's possible to modify a digital camera to take infrared photographs, by removing the infrared filter and replacing it with one that blocks out everything but infrared (made from material obtainable from photographic retailers). It's not recommended that you do this to any camera you'd mind destroying if the procedure fails, but if you are successful, you get something that takes photos like these:
2006/8/13
An enterprising hacker, noticing that his Nokia 6230i mobile phone has both an imaging sensor and Bluetooth, much like a wireless mouse, has written a Java applet that uses the phone as a mouse. It's not perfect (the imaging sensor is not designed for focussing so closely, so it needs a high-contrast surface), and currently requires a special custom driver on the computer, though he is working on making it behave like a standard Bluetooth mouse.
The hacker, going by the name of "Pyrofer", also has a number of other projects up, including a 1541-emulating memory card reader for the C64 DTV.
2006/7/6
Cambodians are making the most of their country's dilapidated, partly disused railways by building and running their own trains. The "bamboo trains", comprised of little more than bamboo platforms on wheels, have been running up and down the decaying tracks, helping locals get around.
A tiny electric generator engine provides the power, and the passenger accommodation is a bamboo platform that rests on top of two sets of wheels. A dried-grass mat to sit on counts as a luxury. It would be a white-knuckle ride - if there were actually anything to hold on to.
Low fares add to the appeal, but the service is not without its quirks. There is only one track - so if two trains meet, the one with the lightest load has to be taken off the rails so the other can pass.The authorities have been discouraging this unorthodox form of transport, though without frequent proper train services (Cambodia's tracks are often in too poor quality to support heavy trains and/or rolling stock is in short supply), there is little they can do to stop it.
I wonder whether the model could be adapted to other countries; what if happened if someone in a rural community in, say, Britain or Australia, campaigning for the reopening of passenger rail lines, took the law into their own hands and run guerilla very-light-rail services over the rusting tracks. They'd probably get shut down by the police in short order, though it could make an amusing story.
(via Boing Boing) ¶ 0
2006/6/9
According to this article, there are two ways to compromise computer security by plugging an untrusted USB/FireWire device into a computer.
The first one's the obvious one: somehow convince a user to plug a USB flash drive or similar into their Windows PC, without disabling autostarting. The PC will automatically run whatever program the AUTORUN.INF file on the flash drive tells it to, and this can then do whatever it likes to the PC. Of course, this won't work if the user holds down SHIFT, disables auto-starting or uses a machine with a less-brain-damaged operating system.
The second method is more intriguing. To allow fast data transfers along USB and FireWire buses, such buses implement direct memory access (DMA). What this means is that anything plugged into them can access (or modify) anything mapped into the machine's memory space at the hardware level, bypassing the operating system altogether. Of course, it requires more work (the device has to be an actual programmable computer, and not just a flash drive), but once that hurdle is crossed, the possibilities, as they say, are endless:
Recently a number of computer security researchers realized the tremendous potential of using DMA over FireWire or USB as an attack vector. At the CanSec West '05 conference, Michael Becher, Maximillian Dornseif and Christian N. Klein demonstrated an exploit that used DMA read arbitrary memory locations of a FireWire-enabled system. The exploit was based on an iPod running Linux. For example, they could plug their customized iPod into a victim computer and grab a copy of that computer's screen--not just without the computer's permission, but even without its knowledge!The article goes on to mention that this attack has not been demonstrated on USB devices, only with FireWire. If it works with USB, it could be interesting. I imagine that sooner or later, they'll start making USB chipsets which take steps to filter DMA requests.
Aside: I wonder whether it'd be possible to use such an approach on, say, a PlayStation 2 (which has two USB ports on the front, sitting rather uselessly), or indeed any other notionally tamperproof computer-based device with USB/FireWire ports. If one could access arbitrary memory inside such a device, one could get up to all sorts of mischief.
2006/3/31
If you want a hovercraft, you could always do what this person did and cobble one together for about US$200, using a lawnmower engine and a fan from an air conditioner.
2006/3/24
This is fairly nifty; a piece of software that divides a library of music videos into segments, listens for incoming sound, and plays the segments matching the sound the most closely. It's implemented using C++, Python and Pd, and will be released soon. Until then, you can watch the video, which explains it and demonstrates, playing back beatboxing as disjointed fragments from a MC Hammer video.
(via Music Thing) ¶ 0
2006/3/7
This person is attempting to build a homemade digital Lomo camera, by grafting a Lomo lens onto a camera (an Epson Digital Rangefinder, which sounds a bit too expensive to be something to casually hack). It'd be interesting to see whether he succeeds, and whether the resulting Frankensteinian hybrid really does combine the grungy, ultra-hip Lomo look with the convenience of digital.
If there was a market for a digital camera that takes pictures that look Lomo-like, wouldn't the obvious way to do it be by adding a mode in the onboard firmware which vignettes the edges of the image and fiddles the colours? I wonder whether anyone has written a Photoshop/Gimp plug-in which "Lomo-fies" images.
2006/2/2
 Some hackers have has wired up an Atari 2600 emulator to Max/MSP/Jitter, ending up with a virtual Atari 2600 whose circuitry can be manipulated in lots of ways, creating weird and nifty visual effects:
Some hackers have has wired up an Atari 2600 emulator to Max/MSP/Jitter, ending up with a virtual Atari 2600 whose circuitry can be manipulated in lots of ways, creating weird and nifty visual effects:
The pixels rendered by the Atari 2600 emulator can now be treated as matrix data by Jitter. So, the game screen can be moved about in 3D space, stretched, and mapped to various types of surfaces (a sphere, for example).
Embedded within the Max/MSP programming environment, these manipulation parameters can be changed in relation to a signal, directly tied to music played through MSP.
It also means that a nearly unlimited number of manipulations can be done at the emulation level. Memory accesses can be visualized (including both RAM and ROM), colors manipulated, and synchronization signals tweaked.Of course, it is only usable if you have Max/MSP and Jitter (which cost a lot of money); though perhaps someone will do something like this for Pd?
2006/1/18
First there was Jeri Ellsworth's 21st-century Commodore 64 and the highly hackable TV game it spawned; and now, a Dutch hacker is building an Amiga in a FPGA chip. Dubbed "MiniMig", Dennis van Weeren's project implements the Amiga's custom chips on the FPGA connected to a 68000 and RAM, and uses disk and ROM images stored in a standard FAT file system on a MMC card. At the time of writing, it is close to completion.
2006/1/12
More wacky goings on on Melbourne's trains, as an unidentified woman broke into train public-address systems, and proceeded to describe her sexual fantasies about the drivers in explicit detail; this happened during peak hour, with hundreds of commuters hearing it, though no witnesses seem to have seen her. Police are at a loss to how she did it, though it is believed she actually got into a vacant train cabin. (I wonder whether this sort of thing is now covered under anti-terrorism legislation.)
(via bOING bOING) ¶ 0
2005/11/12
A hardware hacker with a very steady hand builds a head-up computer display into a pair of slim-line sunglasses. His ultimate goal is to fit sunglasses, a video camera and a microphone, covertly, into what looks like an ordinary pair of sunglasses, effectively making a Snow Crash-style gargoyle rig (just add a wearable computer).
2005/10/15
A user of the social-network site MySpace has found a novel way of making lots of friends: by inserting a piece of JavaScript code into his page which caused all viewers to friend him:
The next step was to simply instruct the Web browser to load a MySpace URL that would automatically invite Samy as a friend, and later add him as a "hero" to the visitor's own profile page. To do this without a user's knowledge, the code utilized XMLHTTPRequest - a JavaScript object used in AJAX, or Web 2.0, applications such as Google Maps.
Taking the hack even further, Samy realized that he could simply insert the entire script into the visiting user's profile, creating a replicating worm. "So if 5 people viewed my profile, that's 5 new friends. If 5 people viewed each of their profiles, that's 25 more new friends," Samy explained.For a brief time, Samy had more than one million new friends. Then MySpace noticed that something strange was happening, shut the site down and cleaned the script off users' pages. Google's Evan Martin has an analysis of the code.
2005/8/8
Impressive hack of the day: turning a Nintendo DS into a GPS-enabled map viewer, using a GPS unit wired to its serial port and a CompactFlash card full of map tile images purloined from Google Maps.
The use of downloaded Google Maps tiles is interesting; I wonder how long until someone writes a map viewer for PalmOS which uses these, effectively cutting into the market share of programs like Tube (which have limited coverage, and often annoying qualities such as being unable to scroll between map tiles; a pain when you're looking for somewhere just off the map, or in the intersection between two tiles). Then again, Google may be able and/or obliged to use the DMCA against any software which attempts to use its map tiles in this fashion (though I am not a lawyer).
2005/6/2
Paul Slocum converts dot-matrix printers into musical instruments, by reprogramming the EPROMs; the resulting instruments use the print head, paper feeder motors and internal beepers to play music, of which MP3s are provided (this one is probably the best). And then there's the Mellotron-like contraption made of a printer, a Walkman and a length of cassette tape.
2005/5/13
Not that long ago, a joystick-shaped device named the C64 DTV, containing a Commodore 64-compatible computer (developed by Jeri Ellsworth, who also created the C-One super-C64) and 30 games, appeared on the market. Hackers who bought these are now opening them up and adding things to them; for one, it is possible solder on a PS2 keyboard (unlike the original C64, this one speaks the PS2 keyboard protocol) and, indeed, a standard Commodore serial bus connector for plugging in a drive (photos here); alternatively, one can embed a DTV inside a working Commodore floppy drive. With a keyboard and storage, the diminutive box (costing US$20, or about 3 times as much in the UK) becomes a fully usable Commodore 64, except for a few additional augmentations, such as a video chip capable of 256 colours. And there is more information on undocumented features of the DTV here.
2005/3/25
Got an empty room, some free time and the urge to amuse and confuse visitors? Why not make a sideways room?
(via bOING bOING)
2005/3/14
Hack of the day: how to make a common USB webcam see in infrared. Executive summary: it involves pulling it apart and replacing the infrared-blocking filter with a piece of exposed photographic film (which blocks visible light though lets IR through).
2005/3/4
Apple's new PowerBooks now contain a motion sensor, allowing them to detect if they're falling and brace for impact. The sensor in question detects not only acceleration but also the machine's tilt. Über-hacker Amit Singh has figured out how to query this sensor and written programs which use it, including a demo which rotates windows on the desktop to compensate for the laptop's orientation.
2005/2/28
Limor Fried, the designer of the home-made Altoids-tin MP3 player and television-sensitive sunglasses, has done it again, with a honest-to-goodness DIY analogue TB-303 clone. The x0xb0x, as she calls it, is apparently as close to a real 303 as one can get; Fried and her collaborators actually took apart a 303 and analysed the characteristics of all the components. Where it differs from a 303 is that it has USB and MIDI (and can be, literally, computer controlled), can control external synths, and has extra modes in the firmware. The unit will be available in kit form for around US$300 (about £160 or A$400); additionally, the designs will be released as open-source, which means that if you can source the exotic transistors used in it (and a list is given), you can make your own.
Also from MusicThing, Led Zeppelin drum outtakes, studio-clean and (apparently) free for the sampling; now you too can sound like the early Beastie Boys. And Casio keyboard boomboxes.
2005/1/20
Interesting technical factoid of the day, from this page: (via /.)
Did you know your 10D and 300D run DOS? That's right. Embedded in the camera is DataLight's ROM-DOS. In fact, if you use the right tool such as s10sh you can see that inside the camera is an A: and B: drive. On the A: drive reside command.com and autoexec.bat, and most interestingly, camera.exe.And this page has a tool for getting a shell on your camera, and gives a list of Canon camera models known to work with it. Unfortunately, I left the USB cable for my PowerShot G2 in Australia, so I can't try it out.
2004/12/21
Several German cities have a phone-based bicycle rental service, in which electronically-locked bicycles are left in the street and may be ridden for 6 Euro cents a minute. This was not good enough for some h4x0r d00dz, so they opened one up and changed the firmware, giving them free rides. (via Slashdot)
Meanwhile, apparently there are secret cheat codes for Coca-Cola vending machines; pressing a certain sequence of buttons puts the machine into a debug menu. From there, one can apparently do fascinating things like, um, seeing how much money the machine has taken and how many cans it has sold. (via bOING bOING)
2004/11/18
Last night, I went to Dorkbot). It was a bit of a mixed bag; the presentation on London Free Map (a sort of geospatial Wikipedia, consisting of people with GPS units walking the lengths of streets to build up a GFDL/CC-licensed map of London and break the Ordnance Survey monopoly; connected with OpenStreetMap) was interesting, as were some of the "minidorks", including one by a chap who put a Wacom tablet on a guitar-like mount and used it to make noise with Max/MSP, and one by an American who built a 3D voxel display for Burning Man, using 729 microcontrollers, RGB LEDs and ping-pong balls, and an Ethernet printer server to control them). Others left a bit to be desired; the architecture student who started his with footage of the World Trade Center attack and went on to talk about the acoustics of spaces, sticking microphones into his mouth and filling latex balls with white noise, seemed a bit on the random side, while the presentation about the possibility of a bicycle that folds into an umbrella-sized package had little more than hastily-made Microsoft Paint drawings to it. There was also an intriguing-looking installation on the table, consisting of a brain-shaped set of neon tubes, a red vintage telephone and a Radio Shack speaker box, though the person operating it couldn't make it, and attempts to demonstrate it over the phone proved inconclusive (all it did was flicker, and the mobile phone interference drowned out what the guy at the other end was saying).
2004/9/10
Somebody has ported UNIX to the GameBoy Advance. Not Linux, UNIX, as in 5th Edition UNIX (1974 vintage), running on a PDP-11 emulator. Mind you, as the GBA has no keyboard and no means to add one, it's not very useful, being limited to executing a sequence of commands compiled into it. But it's impressive nonetheless. (via bOING bOING)
2004/8/5
This sounds immensely cool: two people are writing a book for O'Reilly's Hacks series on taking advantage of the quirks of one's brain. Or, as Cory Doctorow says, a guide for overclocking your amygdala:
I'm talking about minute-by-minute stuff: This is why you scratch your face when somebody else does. This is what will grab your attention in the corner of your eye, and this is what won't. Why the status icons in the corner of your desktop should be black and white and not in colour. That's what Brain Hacks is about, letting you see how all that works, from a standing start.
There's so much I want to say right now. From what I've learned, and the way it's changed how I look at the world - I can now follow the way my attention gets attached to the internal and external world, anticipate what's going to cause subliminal behaviour, and induce it in other people (but don't tell them I've been doing that), oh and the philosophical implications too - to the process: our use of a wiki for research and organisation (the most successful usage I've seen), the pitch process, the nature of writing, writing under pressure, re-learning how to follow citation trails, balance opinions. That can all wait.
2004/6/18
2004/6/16
Formulaic music isn't just for the teeny-boppers and pissed-off teenagers. Computer scientist and songwriter Loren Jan Wilson develops a system to analyse Pitchfork music reviews, finding which words have the most positive connotations, and then using that to write two songs, scientifically designed to appeal to the coolsies who write for Pitchfork.
There are positive values for "rough" and "primitive," and negative values for the words "shiny" and "polished." This points towards a preference for lo-fi recordings, which are usually associated with lower-budget independent music. This falls in line with the Pitchfork reviewers' dislike of capitalism, which I talk about a bit in the other interesting results section below.
The "sadness" group is by far the highest-scoring mood, beating the next mood ("dark") by over 1100 points. As a response to that, I've tried to make these songs as sad as possible.
The songs, Kissing God and I'm Already Dead are provided with MP3 form, along with detailed descriptions of how the analysis guided his creative decisions. The songs, as you'd expect, combine gloomy lyrics, lo-fi guitars, choppy beats and layers of effects.
It'd be interesting if he had gotten Pitchfork to review these songs before revealing their origin, if only to see whether he'd have been critically lauded as the next Radiohead or whatever.
2004/5/27
2004/3/7
Video Feedback Fractals; fractal-looking shapes (resembling IFSes, for the most part) generated using purely analogue means, i.e., a video camera, two monitors and a pane of glass. Which is rather clever. (via Gimbo)
2004/1/14
As of today, I have a 40Gb* Archos Jukebox Recorder 20.
 This Sunday, I went to the computer swap meet and picked up a 40Gb notebook hard disk (a Hitachi TravelStar, for what it's worth), along with a notebook-drive-to-IDE-cable adaptor. Yesterday, I wandered down to Jaycar and bought a set of Torx screwdrivers (that's the funny hexagonal screws used to fasten things that people with ordinary household screwdrivers have no business in opening) and an antistatic wrist strap (just in case).
This Sunday, I went to the computer swap meet and picked up a 40Gb notebook hard disk (a Hitachi TravelStar, for what it's worth), along with a notebook-drive-to-IDE-cable adaptor. Yesterday, I wandered down to Jaycar and bought a set of Torx screwdrivers (that's the funny hexagonal screws used to fasten things that people with ordinary household screwdrivers have no business in opening) and an antistatic wrist strap (just in case).
First, I copied the contents of the Archos to the new disk; I used the adaptor to attach the disk to my Linux box (as /dev/hdb; to make it into the slave device, I borrowed a jumper from an ancient SCSI hard disk I have lying around whose exact origins are lost in the mists of time). I then partitioned it (making one big FAT32 (LBA) partition, as on the Archos), and copied the Archos' contents to it in one gulp, with:
dd if=/dev/sda1 of=/dev/hdb1
Then I used GNU Parted to resize the partition (and the FAT filesystem on it) to take up the entire span of the new disk.
Then came the hardware modification; off came the "Warranty Seal" sticker, and the rubicon was crossed. I was working from this guide, which, whilst written for older Archos units, was quite accurate. The operation was easier than I feared; I was half-expecting the Archos hardware to be next to impossible to take apart without destroying some delicate connection or other, but this turned out not to be the case. The most tricky thing was putting on the black rubber bumpers when putting the case back together (obviously, whoever designs cases for Archos is not the same person who designed the Apple Macintosh G4 case or any similarly hacker-friendly hardware enclosure). In any case, everything went smoothly and without a hitch. I'd say that changing the hard disk in an Archos Jukebox isn't much harder than doing so inside a generic PC; if your warranty has expired (or would involve shipping the unit to France by courier or something similarly useless), it's worth a try.
Now I've got a 20Gb hard disk full of MP3 files, waiting to be recycled. In an ideal world, someone would sell external USB drive enclosures (like the ones you can buy for hard disks) with built in MP3-player functionality. (I believe there are all-in-one MP3 decoder chips that can talk to an arbitrary IDE disk.) Though if those don't exist, I may just end up using it as a backup device or somesuch (the usual fate of old hard disks).
* That's in marketing gigabytes. It actually has 37Gb or so of space, though that is still twice its former capacity.
2003/10/29
Motorists in the U.S. will soon be able to buy a device that turns traffic lights green. The device will cost about US$499 and interface with the infrared receivers at intersections that allow emergency vehicles to change the lights. Think of how much quicker you'll get that pizza when the pizza guy has one of those babies on his dashboard... (via FmH)
2003/10/9
A Mini-ITX novelty project with a difference, Bass Station is an oversized 1980s-style ghetto blaster containing a Linux-based Mini-ITX PC which plays MP3s. Not only that, but it contains an 802.11 access point and web server, making an instant collaborative jukebox, file server and bulletin board for all within range. (via bOING bOING)
2003/9/22
If those IBM-style tactile keyboards aren't solid and mechanical enough for you, you could always try converting a mechanical typewriter into a PC keyboard. Then all you'd need would be a small black and white monitor with a Fresnel-lens magnifier in front of it, and you'd have retrocomputing à la Brazil. (via VM)
(I wonder whether it would be possible to fit a Mini-ITX-based computer inside a working mechanical-typewriter-based keyboard. That would be pretty doovy...)
2003/7/8
Meet Hektor, a Swiss-designed spraycan graffiti robot, or possibly one of the world's largest portable inkjet printers. (Note that it's not the largest, as the BBC piece suggests; I recall a larger version of GraffitiWriter, one of Hektor's predecessors, mounted on the underside of a van, and used to inscribe dot-matrix slogans on roads.)
2003/7/7
Introduction to Reverse Engineering Software; a big book on how to pick apart compiled programs (Intel-centric; mostly Linux-specific, though with some Windows info as well). For lawful uses only, of course.
2003/6/26
Some hackers in France have written a multitasking GUI-based OS for the Intellivision game console; that's an old TV game box from the 1980s, based on a bizarre CPU nobody else used). Which looks about as useful as the various attempts at Commodore 64 UNIX.
2003/5/25
This is pretty cool, in a UNIX-geek sort of way: using the LPD printer spooler as a MP3 jukebox. In short, you set up a "printer" which plays MP3s (or other music files) and then "print" MP3s to it (from the local machine or remote machines). (via Slashdot)
2003/5/21
The account of the steam-powered drum machine, or rave culture meets steampunk:
Soon after the crowd had entered, the doors were locked tight so as to prevent intrusion from representatives of the Law. Van Hoovenaars then unveiled a huge and terrifying contraption. A multitude of brass pistons, steam cylinders and horns had been fashioned together, as like the internal frame of a fire-spewing Behemoth burst forth from teutonic myth. The professor addressed his audience, explaining that each piston reverberated on to a canvas of varying thickness to produce a series of rythmatic beats. He warned the gathering that once set in motion the machine "would produce such rhythms that man has never dared imagine - over an eleven hour period".
(via MeFi)
2003/2/24
First there was the C-One, the Commodore 64 of the future, and now some hackers are using FPGA chips (i.e., dynamically reconfigurable hardware) to reimplement old arcade game boards, all on a chip; just supply the ROMs. The FPGA designs apparently even have extra "code" to convert the arcade-video-monitor signals to VGA, for those who don't have one of those big glass bottles sitting around. (via Slashdot)
(This is cool, not just because of the hipness of the the retro-video-game thing; the fact that you can make a small FPGA chip emulate any digital circuit, from a Pac-Man board to a Commodore 64 with an IDE interface bolted onto it, all by downloading the right information into it, is very cool. Now you have hackers creating open-source "hardware" components for FPGAs; i.e., code which, when integrated into a project, makes a complete 6502 core or USB interface or whatever, and others bolting them together to make all sorts of highly miniaturised gadgets. Unfortunately, FPGAs seem to only work for digital circuits, so something like a purely analogue open-source TB-303 core (suitable for embedding into mobile phones, childrens' toys and other gizmos) would not be possible.)
2002/12/11
Update: I've compiled vstserver and the k_vst~ Pd object and (after some hacking) have managed to get VST plugins working under Linux. Things are still a bit flaky (for some reason, vstserver refuses to recognise plugins anywhere but the current directory it's run from), but I've now got the familiar mda Combo plugin crunching up an Amen Brother break, all in a Pd patch under Linux. Life is good.
2002/8/16
The story of how a team of math geeks from MIT hacked Las Vegas blackjack, developing a team-based card-counting method that raked in huge profits and evaded the casinos' usual countermeasures -- for a while, anyway. (via Plastic)
2002/8/4
This looks doovy: One enterprising hacker has developed an Atari 2600-based musical instrument cartridge. The Synthcart has beats and arpeggiators, and can be operated without a TV. Wonder how long until we see Ataris take the stage next to circuit-bent Hello Kitty toys and GameBoys running NanoLoop. (via Slashdot)
2002/7/28
These people sell modern PCs retrofitted into old Amiga 1000, Atari 2600 and Nintendo Entertainment System cases. And they come with emulators for the original machines. (Except that the PC's disk drive, of course, won't read Amiga floppies, and I doubt that they've interfaced the cartridge ports on the Atari and NES cases to the emulator software. If they had, it'd be pretty doovy.) (via Slashdot)
2002/7/4
Chinese-based spiritual movement/terrorist group (depending on whom you believe) Falun Gong have reportedly hacked one of China's main TV satellites, broadcasting a pro-Falun Gong banner on TV channels. (Mind you, this news comes from The Australian, a publication of News Corp., whose executives have outspokenly condemned Falun Gong and defended the Chinese government's hard line against the group. Make of that what you will.)
2002/6/25
Somebody has written a plug-in for the Linux xmms media player to allow it to use Winamp visualisation plugins, using the Wine Windows emulation library. Which is fairly nifty. Now if only someone wrote a Linux library for accessing Windows VST audio processing/synthesis plugins, perhaps in the aRts or LADSPA framework...
2002/3/28
CodeWeavers, who wrote the CrossOver web browser plug-in for Linux (which allows Windows plug-ins to run under Linux) have now released a system for running MS Office on Linux. Which is technically a fairly impressive feat; equally impressively, all the code has been contributed back to WINE, the LGPLed Windows emulation system for Linux; which means that, after all these years, WINE may be becoming more than a technical curiosity. (It's certainly better than things like Lindows, as (a) it isn't based on a customised, dumbed-down Linux distribution, and (b) the code is going back to the community.) (via Slashdot)
2002/3/22
Sokoban in sed! And it's quite playable too, if you don't depend on advancing to the next level automatically. (via Slashdot)
2002/1/18
Remember when ProDOS wasn't just a Randroid loony? Retrocomputing hack of the day: One enterprising hacker is working on a CompactFlash IDE adapter for the Apple II; one which will give up to two 32Mb ProDOS volumes per CF card. (Or IDE hard disk for that matter.) (Via Slashdot)
2001/10/25
These people make improvised electronic musical instruments (with names such as the "Pikachu Glitch Synthesizer") out of toys and other devices. Pretty doovy. (via Slashdot)
2001/6/3
The amazing story of childhood prodigy David Hahn, who built a nuclear reactor in his garden shed at age 15.
Of his exposure to radioactivity he says, "I don't believe I took more than five years off my life."
(via Slashdot)
2001/1/26
Life imitates cyberpunk scifi; or at least this account of the cat-and-mouse game between digital satellite TV company DirecTV and rogue hackers, does. It even reads like a story; the hackers kept cracking DirecTV's cards, one by one, but ultimately were defeated with cunning and no small measure of style. (via Slashdot)
2001/1/20
Retrocomputing meets chindogu: Someone in the UK is designing an updated ZX Spectrum compatible, using only off-the-shelf parts. The SpeccyBOB, as he calls it, will be mostly Spectrum compatible, though will have 4Mb of RAM and an IDE hard disk interface. Watch the web site for circuit diagrams and such.
2000/11/8
When Lego released its programmable Mindstorms kits, they were reverse-engineered pretty quickly by hackers dissatisfied with their limitations. Rather than send in the lawyers, Lego's policy was to condone this. As a result, the Mindstorms kits have sold like hotcakes as hackers have taken to them.
2000/10/29
Via Slashdot, a piece on how Intel Pentia are microcode upgradeable. The details are kept secret at this stage, though once someone cracks them this could lead to a new generation of viruses/trojans which irrevocably turn CPUs into expensive keyrings.
2000/10/23
Interesting software du jour: Mac-on-Linux, which allows you to run MacOS in a window on top of Linux/PPC (a bit like SheepShaver, only this one is GPLed). I should probably have a look at it at some stage (if I decide to play with Linux/PPC once I get more disk space on my Mac); though I probably wouldn't end up using it much (I suspect Cubase VST probably wouldn't run on it as efficiently as on MacOS alone).
2000/7/20
Marketing ploy of the day: ASUS, manufacturer of 3D graphic accelerator cards favoured by computer gamers, have hit upon a clever way of boosting the sales of their brand: offering the cards with a driver which allows you to see through walls, thus giving ASUS-based players of first-person shooters an unfair advantage over those using rival cards. However, the public didn't like this idea much, and the driver was withdrawn.
2000/4/23
1999/10/27
Insanely cool, or perhaps vice versa: Now you can play classic arcade games on a Kodak digital camera. (via Slashdot)